All Cfp Share URL
Thursday, February 3, 2022
Low Power Low Voltage Bulk Driven Balanced OTA
Handling Trust in A Cloud Based Multi Agent System
Cloud computing is an opened and distributed network that guarantees access to a large amount of data and IT infrastructure at several levels (software, hardware...). With the increase demand, handling clients' needs is getting increasingly challenging. Responding to all requesting clients could lead to security breaches, and since it is the provider's responsibility to secure not only the offered cloud services but also the data, it is important to ensure clients reliability. Although filtering clients in the cloud is not so common, it is required to assure cloud safety. In this paper, by implementing multi agent systems in the cloud to handle interactions for the providers, trust is introduced at agent level to filtrate the clients asking for services by using Particle Swarm Optimization and acquaintance knowledge to determine malicious and untrustworthy clients. The selection depends on previous knowledge and overall rating of trusted peers. The conducted experiments show that the model outputs relevant results, and even with a small number of peers, the framework is able to converge to the best solution. The model presented in this paper is a part of ongoing work to adapt interactions in the cloud.
For more details:https://allconferencecfpalerts.com/cfp/view-paper.php?eno=5261
Wednesday, February 2, 2022
PERFORMANCE ANALYSIS OF HYBRID FORECASTING MODEL IN STOCK MARKET FORECASTING
Author : Mahesh S. Khadka*, K. M. George, N. Park and J. B. Kima
Affiliation : aDepartment of Economics and Legal Studies in Business, Oklahoma State University, Stillwater, OK 74078, USA
Country : USA
Category : Information Technology Management
Volume, Issue, Month, Year : 4, 3, August, 2012
Monday, January 31, 2022
Low Power Low Voltage Bulk Driven Balanced OTA
The last few decades, a great deal of attention has been paid to low-voltage (LV) low-power (LP) integrated circuits design since the power consumption has become a critical issue. Among many techniques used for the design of LV LP analog circuits, the Bulk-driven principle offers a promising route towards this design for many aspects mainly the simplicity and using the conventional MOS technology to implement these designs.
For more details:https://allconferencecfpalerts.com/cfp/view-paper.php?eno=5276
Wednesday, January 26, 2022
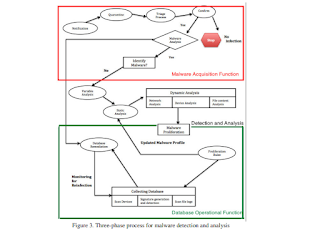
Optimised Malware Detection in Digital Forensics
Author : SaeedAlmarri
Affiliation : University of Bedfordshire
Country : United Kingdom
Category : Networks & Communications
Volume, Issue, Month, Year : 6, 1, January, 2014
Abstract :
Keyword : Denial of service (DOS), Wireshark, Netstat, TCPView, The Sleuth Kit (TSK), Autopsy, Digital Forensics, Malware analysis, Framework
Sunday, January 23, 2022
Classification of OCT Images for Detecting Diabetic Retinopathy Disease using Machine Learning
Author : Marwan Aldahami and Umar Alqasemi
Affiliation : King Abdulaziz University
Country : Saudi Arabia
Category : Digital Signal & Image Processing
Volume, Issue, Month, Year : 12, 6, December, 2021
Abstract :
Keyword : Image classification, diabetic retinopathy, support vector machine, optical coherence tomography, retina, machine learning.
For more details: https://allconferencecfpalerts.com/cfp/view-paper.php?eno=5274
Monday, January 17, 2022
Sensing Method for Two-Target Detection in Time-Constrained Vector Poisson Channel